The information contained here is offered by the author as a set of guidelines to protecting home computers and networks from unauthorized use across the Internet. The suggestions listed here do not necessarily represent any organization with which the author is affiliated but are provided here as a public service.
This page provides some suggestions to secure small office, home office, and home connections to the Internet. These rules apply to both dial-up and dedicated (DSL/cable modem) access. This document will address the following items, which are essential for securing your home systems; there is still more to do after these steps are completed but they will get your started:
- On Windows systems, unbind file and print sharing from TCP/IP
- Use anti-virus software
- Employ some type of firewall software or hardware
- On Windows systems, be sure to display file extensions
- Never open an attachment unless it comes from someone you know and you are expecting it
- Turn off Java, JavaScript, ActiveX, etc. on your browser unless you are at a known, "safe" site
1. Unbind file and print sharing from TCP/IP
The most dangerous issue for any computer running any version of the Windows operating system is that file and print sharing is, by default, enabled and bound to TCP/IP. That means, simply, that the same capability that allows peer-to-peer networking and file sharing on your home/office LAN is available to anyone on the Internet!! In particular, the following ports are open and listening:
- UDP port 137, nbname (NetBIOS name service)
- UDP port 138, nbdatagram (NetBIOS datagram service)
- TCP port 139, nbsession (NetBIOS session service)
There is no reason for file and print sharing to use TCP/IP. Before connecting in any way to the Internet, Windows users should block file and print sharing over TCP/IP. This is simply done; go into the Network configuration under Control Panel, and unbind "Client for Microsoft Networks" and "File and print sharing for Microsoft Networks" in the TCP/IP properties for all adapters using TCP/IP (Screen #1). You can still do all of the file and print sharing that you want over the LAN because Microsoft networks use the NetBIOS protocol and don't need to have these functions bound to TCP/IP.
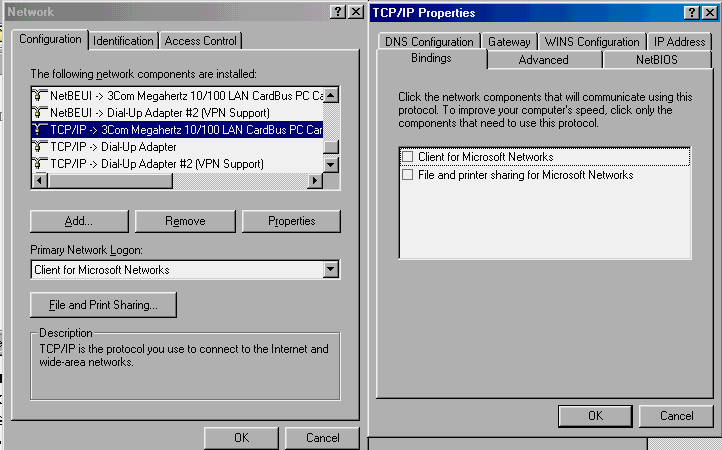
SCREEN 1. TCP/IP Properties dialog box, showing how to unbind "Client for Microsoft Networks" and "File and print sharing for Microsoft Networks" from the TCP/IP protocol associated with the LAN adapter. |
The situation is somewhat clouded in Windows 2000, however. With that operating system, Microsoft decided that TCP/IP was the only communications protocol to employ so that file sharing has to use it. In this case, you will find TCP port 445 open on your computer.
Although counter to Microsoft's wishes, my advice (consistent with many others) is to install the NetBEUI protocol onto your Windows 2000 system and then unbind file and print sharing from TCP/IP.
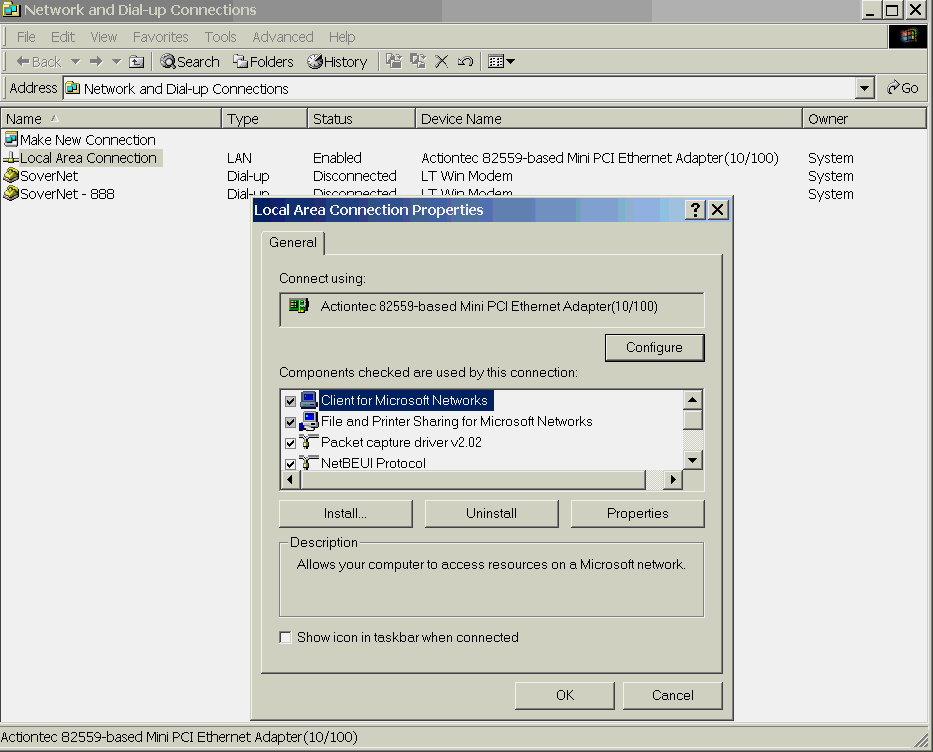
SCREEN 2. Local Area Connection Properties dialog box, showing how to install the NetBEUI protocol. |
To install NetBEUI in Windows 2000 (Screen #2):
- Open the Network and Dial-Up Connections dialogue box.
- Right-click on Local Area Connection and select Properties.
- Click the Install button.
- Click on Protocol and then click the Add... button.
- Click on the NetBEUI Protocol and then click the OK button.
- Click the OK button on the Properties dialogue box to finish.
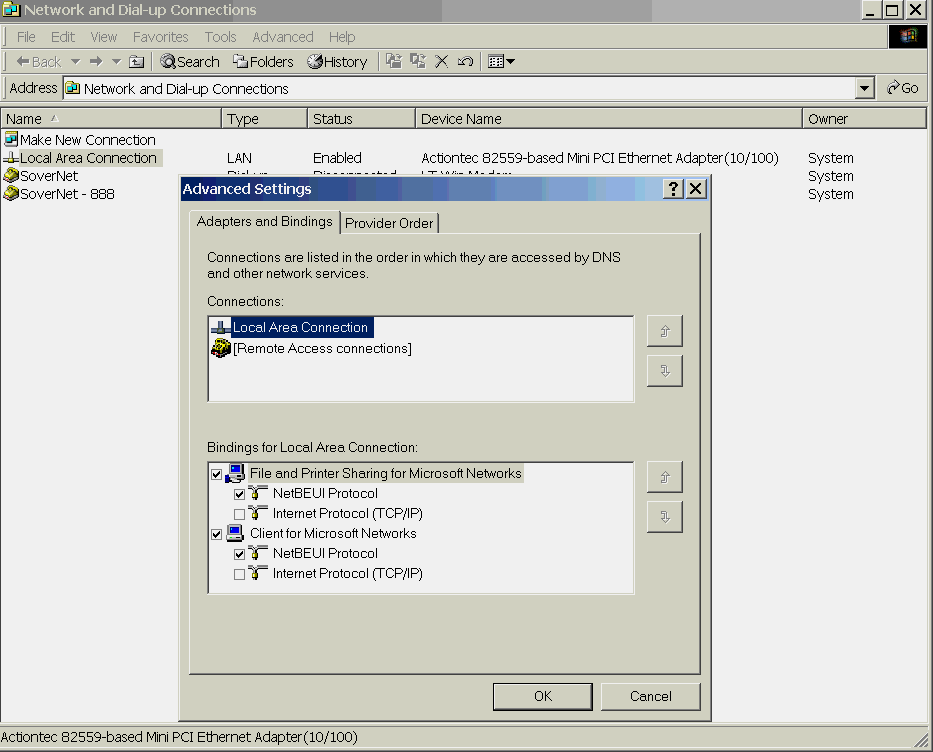
SCREEN 3. Advanced Settings dialog box, showing how to unbind "Client for Microsoft Networks" and "File and Print Sharing for Microsoft Networks" from TCP/IP. |
To unbind file and print sharing from TCP/IP in Windows 2000 (Screen #3):
- Open the Network and Dial-Up Connections dialogue box.
- Select the Advanced pulldown menu and choose the Advanced Settings... option.
- Uncheck the TCP/IP box under the "File and Print Sharing for Microsoft Networks" and "Client for Microsoft Networks" bindings, then click the OK button.
NetBEUi does not ship at all with Windows XP. To install NetBEUI on a Windows XP system, see Microsoft Knowledge Base Article Q301041.
2. Employ Anti-Virus Software
It is imperative that all users on the Internet run and maintain anti-virus (AV) software. Installing AV software alone is not sufficient; users also have to use the option to run the software at all times (sometimes called auto-protect) and to routinely update the AV signature files. There are well over 50,000 known virus signatures today and that number continues to grow; AV software vendors generally update their signature database file at least weekly. If your software has the option, consider having the software automatically check the vendor's Web site for update and automatically download and install new signature files when they are available (sometimes called live update). Note that although the vast majority of viruses target Windows operating systems, Mac, Unix/Linux, and other operating systems are not immune.
There are many vendors of AV software, some of which are listed below; costs vary but US$35-50 is a rough estimate. Obtain a reputable product; AV software on your PC is often your first and only defense against viruses:
- AntiViral Toolkit Pro (AVP) — www.avp.ch/avpve
- F-Secure — www.f-secure.com/virus-info
- McAfee Anti-Virus — www.mcafee.com/anti-virus/
- Norton AntiVirus — www.symantec.com/avcenter/
- Sophos Anti-Virus — www.sophos.com/products/software/antivirus/
- Trend Micro PC-cillin — www.antivirus.com/vinfo/
3. Employ a Personal Firewall
If you are on the Internet, you should use some form of personal firewall. Personal firewall software runs on your computer and protects against attempts by outsiders to break into your computer. If you have a LAN at home, a hardware firewall might make more sense both economically and practically; most home hardware firewalls also double as a LAN hub/switch and personal firewall software might block local peer-to-peer networking which you want. You will need one copy of personal firewall software for each machine that you want to protect, while a single hardware firewall can protect all systems on the local network.
Some of the available personal firewall software products for Windows are listed below; prices vary from free to US$90. Good, independent reference information for choosing personal firewall software can be found at the Home PC Firewall Guide (www.firewallguide.com).
- BlackICE PC Protection — http://blackice.iss.net/product_pc_protection.php
- ConSeal PC Firewall — www.consealfirewall.com
- CyberArmor Personal Firewall — www.cyberarmor.com/products/pf/index.html
- Internet Firewall 2000 (IFW2000) for Personal Computers — www.digitalrobotics.com/IFW2000.htm
- Norton Personal Firewall & Norton Internet Security — www.symantec.com/consumer_products/home-is.html
- Tiny Personal Firewall and WinRoute — www.tinysoftware.com
- ZoneAlarm — www.zonelabs.com/
There are also a number of cable modem/DSL hardware products that provide firewall capabilities; prices here range from about US$75-200:
- D-Link home broadband products — www.dlink.com/products/DigitalHome/Broadband/
- Linksys EtherFast Cable/DSL Router family — www.linksys.com
- Macsense XRouter family — www.xsense.com/Product/xrouter/index.html
- SonicWALL SOHO2 — www.sonicwall.com/products/soho/index.html
4. Show File Extensions
By default in Windows, Windows Explorer and other Microsoft applications do not show the extension of files if the extension is "known" to the operating system. This is potentially dangerous with the many viruses that are distributed today with a so-called "double extension"; e.g., a file named foo.jpg.exe. This is an executable file because of the .exe extension. If extensions are hidden, however, the user will only see the name foo.jpg and might open this, mistaking it for a JPEG file.
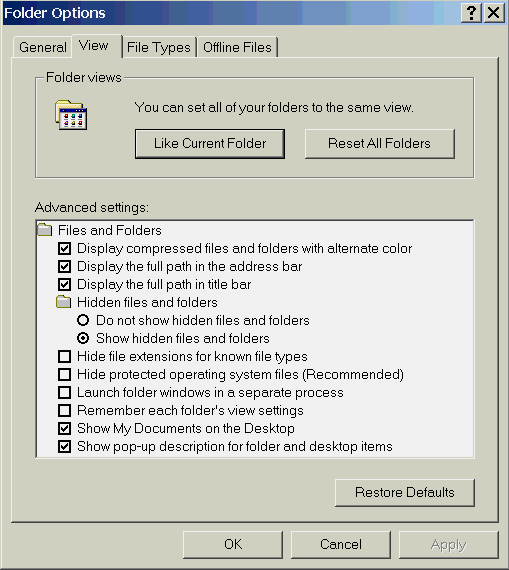
SCREEN 4. Showing file extensions in Windows Me/2000. |
To display file extensions in Windows Me and Windows 2000 (Screen 4):
- Open Windows Explorer
- Choose the Tools submenu and select the Folder Options... option
- Click on the View tab
- Uncheck the box on the "Hide file extensions for known file types" line and click the OK button
In versions of Windows before Windows Me, this function can be found in the Options... option of the View submenu.
5. Take Care Opening Attachments
E-mail attachments are the most common way in which viruses are propagated on the Internet. You should never open an e-mail attachment unless it comes from someone you know and you are expecting it. An attachment coming from someone you know is not sufficient proof that it is ok to open; most of today's viruses and worms use a compromised address book to find new targets.
(The advice to "be expecting" the attachment should also be taken with a grain of salt. I would suggest that the next generation of virus/worm may employ two messages; one telling you to expect a file and the next containing the attachment.)
As a side note, some e-mail software will automatically execute some attachment types when you preview a message; this feature should be turned off, if possible. Outlook and Outlook Express are among the worst offenders in this regard; consider using another e-mail client if you can.
6. Secure Your Browser
Malicious code can be sent to your computer through your browser; Internet Explorer is particularly prone to this so-called malware. Turn off all active-content mechanisms on your browser — Java, JavaScript, and ActiveX — unless you are at a known, "safe" Web site.
About the Author: Gary C. Kessler is an Assistant Professor and program director of the Computer Networking major at Champlain College in Burlington, Vermont, chair of the Vermont InfraGard chapter, and an independent consultant and writer. More information can be found at his Web site at http://www.garykessler.net. His e-mail addresses is kumquat@sover.net.