Cable Modems and the Internet: Securing the SOHO
An edited version of this paper with the title "Securing Cable Modems" originally appeared in the July 2000 issue of Information Security Magazine (www.infosecuritymag.com). Copyright (c) 2000. All rights reserved.
As recently as a few years ago, high-speed Internet access for the small office/home office (SOHO) was still an expensive proposition. The relatively recent emergence of low-cost alternatives such as cable modems and the variety of digital subscriber line (xDSL) technologies, however, has totally changed the calculus, making telecommuting and remote office connections over the Internet a breeze.
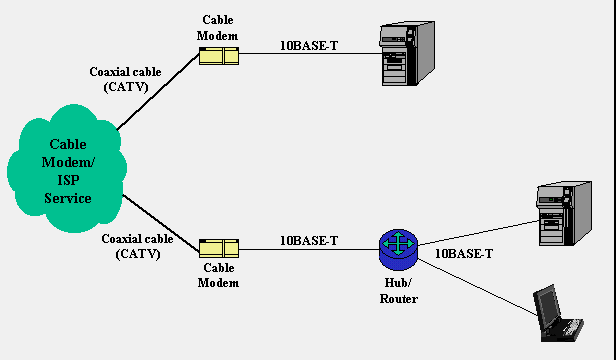
FIGURE 1. Cable modem connection scenarios. The upper topology is most common; a coaxial cable delivers the service to a cable modem which in turn is connected to a computer via a 10BASE-T cable. The lower topology shows the cable modem connected to a hub/router that acts as the connection point for the SOHO LAN.
|
Figure 1 shows the most common network connection topologies when using cable modems. The cable TV company runs a coaxial cable into the building to deliver their Internet service. Although fed from the same coax that provides cable TV service, most companies place a splitter outside of the building and runs two cables in, rather than using a splitter at the set-top box. The coax terminates at the cable modem.
The cable modem itself attaches to the SOHO computing equipment via its 10BASE-T port. In most circumstances, the cable modem attaches directly to a user's computer. If a LAN is present on the premises (something many cable companies frown upon), some sort of router can be connected to the cable modem.
THE RISKS
As these new technologies have rolled out, new security concerns have arisen and even old security concerns become more urgent. Most users of the Internet never think twice about the fact that their computer (particularly a Windows machine) might be totally exposed out on the 'Net; in fact, a nefarious site can examine your system, browse your files, and possibly even overwrite and/or delete information during a dial-up connection via your favorite Internet service provider (ISP). And this threat is quite real; on April 1, 2000 the FBI put out a warning about a virus being spread on the Internet by copying a script to Windows systems where file/print sharing was enabled (http://www.nipc.gov/nipc/advis00-038.htm). This threat may or may not be mitigated somewhat for those users who are only on the Internet for minutes at a time via dial-up modem, but cable modem and xDSL users can now be on-line and connected 24 hours-a-day, everyday. So the exposure of your computer is now very real; a system with a fixed IP address just sitting there without safeguards and possibly with several TCP ports just waiting to accept anonymous connections. In fact, few SOHO users stop to ponder that your home system is as vulnerable as any computer on your enterprise network. And while we spend considerable resources protecting the enterprise, we often overlook the home. Considering how many users take corporate information home to work on, we see that the vulnerabilities to business are very real.
Computers in the SOHO, like those making dial-up connections, are connected to the Internet without benefit of a firewall. There are a number of vulnerabilities that might be exploited from the outside.
First, most computers running TCP/IP — be they a Mac, Unix box, or Windows computer — have some services open that the user may not know anything about. This is particularly true for Unix and Windows NT systems which are very service rich. One way to limit your exposure is to determine what TCP/UDP ports are open by using the netstat -a command and then close those services that you are not using.
Another test of your system's exposure can be found at Steve Gibson's excellent Shields UP! Web site (http://grc.com), where your system will be tested for a number of vulnerabilities such as open FTP, Telnet, SMTP, finger, HTTP, POP3, and IMAP ports.
Second, Windows computers are particularly exposed because file and print sharing is, by default, enabled and bound to TCP/IP. That means that the following ports are open and listening:
- UDP port 137, nbname (NetBIOS name service)
- UDP port 138, nbdatagram (NetBIOS datagram service)
- TCP port 139, nbsession (NetBIOS session service)
This is unnecessary and dangerous. Before getting connected in any way to the Internet, Windows users should block file and print sharing over TCP/IP. This is simply done; go into the Network configuration under Control Panel, and unbind "Client for Microsoft Networks" and "File and print sharing for Microsoft Networks" in the TCP/IP properties for all adapters using TCP/IP (Screen #1). You can still do all of the file and print sharing that you want over the LAN because Microsoft networks use the NetBIOS protocol and don't need to have these functions bound to TCP/IP.
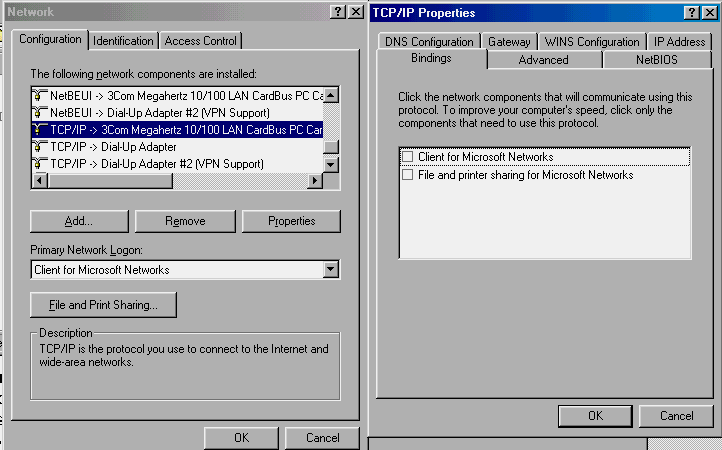
SCREEN 1. TCP/IP Properties dialog box, showing how to unbind "Client for Microsoft Networks" and "File and print sharing for Microsoft Networks" from the TCP/IP protocol associated with the LAN adapter.
|
Finally, many games and other freeware/shareware software packages come complete with Trojan horses. One popular attack is to scan systems looking to see if they can be exploited by known backdoors. Users have to be extremely vigilant when downloading "freeware," you may be getting a lot more than you bargained for.
The cable modem environment has an additional exposure because it is fundamentally a shared medium network. All of the homes that share a cable television coaxial cable segment are on the same cable modem LAN segment as well and, therefore, a user with a protocol analyzer can sniff packets and/or browse the neighborhood (literally!).
While all of these exposures are quite real, there are real defenses as well. I recently obtained cable modem service from my cable TV company, Adelphia, and I am connected to their Internet service (there is no ISP choice when using a cable modem, at least in Vermont; that is a policy issue that I leave for a different magazine). I used the opportunity to learn first-hand about the exposures and what to do about them, as well as to test a couple of different types of security solutions.
It is important to note that there are a number of places in the network where SOHO protection takes place. The sections below will discuss the cable modem itself, firewall software for the computers, and a firewall appliance for the network.
CABLE MODEM SECURITY
Computers that are attached to a cable modem system are exposed to the outside world because they are being networked in a way for which they were not originally intended. The first widely-exploited vulnerability is due to Windows file and print sharing, as described above. The second issue is the shared cable itself.
The third issue revolves around the fixed IP address assigned to the user. If I have a fixed IP address, it means that someone can find me on the Internet over and over. For that reason, most cable ISPs use the Dynamic Host Configuration Protocol (DHCP) to dynamically assign an address and the lease period is purposely kept short; my ISP uses 3-hour leases. But this doesn't solve any problem for systems that stay connected all the time. With a 3-hour lease, my computer (or hub) requests renewal of the address assignment every 90 minutes and the DHCP server always grants the request. Since my network stays connected whether my computers are on or not, my IP address never changes. (I counter this by periodically releasing the assignment and waiting several hours to request renewal.)
But two points need to be made. First, you can't easily hide your IP address from the masses in any case. Sending me a nice e-mail complimenting my article, for example, is sure to get you a reply — which will contain my IP address and host name in the header. So changing my address periodically still doesn't keep it a secret although it may protect me from someone purposely looking for me. Second, so many of the attacks these days are not targeted anyway; attackers merely troll for victims by scanning a NET_ID range (the updated version of war dialers that would dial every telephone number in a range looking for modems).
Security in this environment, then, begins at the cable modem itself. The cable industry has adopted the Data Over Cable System Interface Specification (DOCSIS) as the de facto standard for cable modem operations, including secure communications. The Baseline Privacy (BPI) specification is one of the DOCSIS security options that addresses the potential problem of packet sniffing. The BPI specification calls for encrypting user packets with the Data Encryption Standard (DES) and use of 768-bit RSA for key exchange. Although DES was shown to be susceptible to a brute-force attack in 1998, around the time that DOCSIS was adopted, DES is certainly sufficiently secure against the pedestrian hacker and frequently changing the key makes it even safer. Nevertheless, the BPI standard will probably employ the Advanced Encryption Standard (AES) once it is adopted this year or next.
My cable modem, by the way, is a Bay Networks Versalar Cable Modem 100. It also came pre-configured to filter most "dangerous" TCP/IP ports and even non-IP protocols, including NetBIOS, AppleTalk, and NetWare's IPX.
A SOFTWARE FIREWALL
My initial connection to the cable ISP was with a single computer. To provide protection for this machine, I decided to obtain a simple software firewall; this decision was partially economic since the software solutions range in cost from free to $80 or so.
For this trial, I used Network ICE Corp.'s BlackICE Defender (http://www.networkice.com/). BlackICE is not only a "personal" firewall but also offers intrusion detection reporting. Designed for Windows 95/98/NT, the NetworkICE Web page claims that "BlackICE Defender offers INSTANT INSTALLATION, no configuration necessary, making it a product for the masses." The truth is that this claim made me a little nervous because I really don't believe in plug'n'play security solutions; even the smallest office should have some idea of what they want to accomplish security-wise and that should dictate security policy rather than the tool dictating policy.
Nevertheless, BlackICE is as near to PnP as they claim and installation was a snap. Furthermore, the default settings are, in my opinion, quite appropriate for a SOHO looking to protect itself on the dark alley that is the Internet; Microsoft could learn a big lesson here in delivering software with prudent precautions enabled rather than every security mechanism disabled by default.
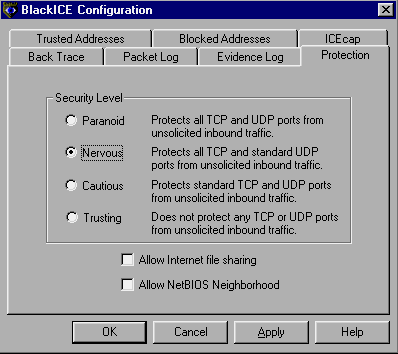
SCREEN 2. The BlackICE Configuration Protection tab. Here I have selected the Nervous security level with sharing and neighborhood browsing disabled.
|
The most important part of the BlackICE configuration is the Protection tab (Screen 2). As shown, BlackICE defines four security levels:
- Paranoid: Block all TCP and UDP ports
- Nervous: Block all TCP ports and standard UDP ports
- Cautious: Block all standard TCP and UDP ports (default)
- Trusting: Don't block any TCP or UDP ports
The "standard" TCP and UDP ports are those less than 1024, which are also called privileged ports. The default setting is the Cautious level although I personally prefer the Nervous (or even Paranoid) setting. Trusting (aka "promiscuous") is never warranted for general operation. Separate check boxes allow you to control file and print sharing (TCP port 139) and NetBIOS Neighborhood browsing; the default here is to disable these options.
Even if you don't do anything at all after installing this software, it provides a pretty good degree of protection. When I tested BlackICE using my dial-up modem (thereby no longer protected by my cable modem's filters), the standard ports that were being tested couldn't even be found.
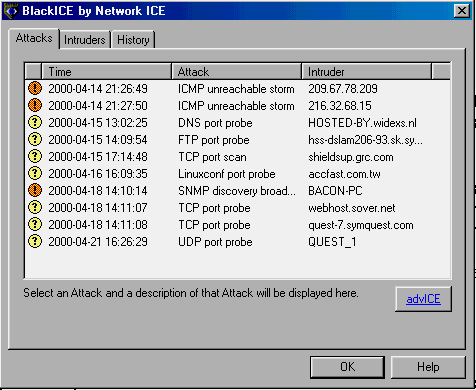
SCREEN 3. The BlackICE Attacks tab shows time, type of attack on your system, and intruder. Clicking on the attack type will provide more detailed information about the attack.
|
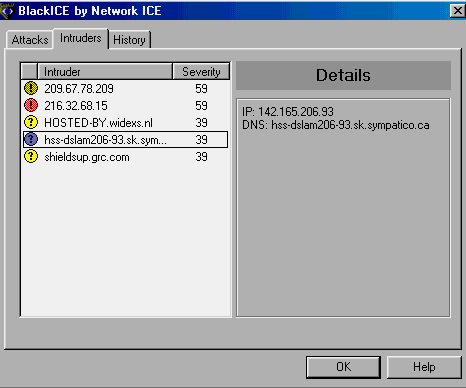
SCREEN 4. The BlackICE Intruders tab shows attacking site and attack severity.
|
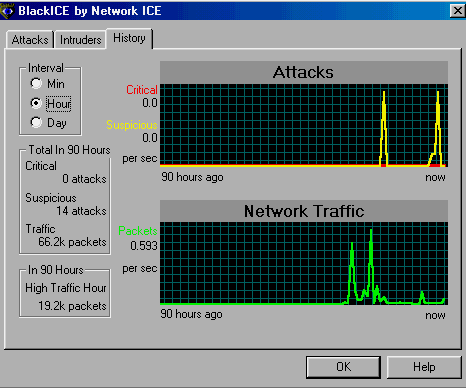
SCREEN 5. The BlackICE History tab shows recent traffic levels and attack packets.
|
While the protective aspects of BlackICE are really neat, the intrusion detection reporting capability is almost more impressive. Although just a reporting feature of the basic software, there's a lot that you can learn:
- The Attacks tab (Screen 3) lists attacks detected by your system by type and source; note the number that I detected over the period of a week and my computer was only intermittently on my SOHO LAN. You can get further information about the individual attacks from the Network ICE Web site by clicking on the advICE button. I initiated four of these attacks on myself (the ones from grc.com, sover.net, and symquest.com) but the other probes on my system came uninvited by unknown persons. The yellow question mark indicates a suspicious event while the orange exclamation point indicates a serious attack; other attacks might be flagged as informational or critical.
- The Intruders tab (Screen 4) lists the intruders and additional information about the source site.
- The History tab (Screen 5) shows the recent network traffic level and numbers of attack packets.
For a personal system, BlackICE provides a lot of information. And it even offers a way to fight back. As shown in Screen 2, there are mechanisms to maintain a simple packet log as well as a more detailed dump of all packet traffic in the evidence log (you need other software to read the evidence log). There is also a backtrace facility which would allow you to work your way back to the source of an attack.
It is easy to block all ports using the BlackICE interface although it is not as easy to block just some ports. For example, suppose you want to put an FTP or Web server on a system protected with BlackICE, in which case you'd like to block all standard TCP ports except FTP and HTTP. You can't do that via the standard configuration mechanism. You can, however, manually edit the .ini file to provide this capability and articles at NetworkICE's Web site show you how to do this. In addition, there is a utility that you can get that allows you to edit the filters via a graphical interface.
A HARDWARE FIREWALL
I have a small LAN in my home office and really wanted to attach the LAN to the Internet via the cable modem. For this, I needed a small router of some sort. Since I was now protecting a network, I decided to get an appliance that handled not only the networking aspects of the connection but also the firewall aspects.
For this scenario, I used Macsense's XRouter Internet Sharing Hub (MIH-120) (http://www.macsense.com). The XRouter was designed for use with cable or DSL modems so is perfect for the SOHO environment. Without dwelling on it's networking features, it is useful to list them:
- Configuration is via the Web browser
- Can be assigned a static or dynamically-assigned public IP address
- Contains an integrated 4-port Ethernet 10BASE-T hub
- Acts as a DHCP server (for a single Class C address, up to 252 LAN hosts)
- Software performs Network Address Translation (NAT)
The XRouter, then, is a nice networking device to hook up many computers in a SOHO to the Internet via a cable modem (or xDSL) connection. Note that NAT may well be a necessity if you have a SOHO LAN because most cable modem Internet services will only assign a single public IP address to a site. This environment clearly needs some sort of firewall protection and the XRouter has some nice features here, too.
Out of the box, the XRouter blocks all unexpected incoming protocol traffic. This is a good default configuration, making this as plug'n'play as the BlackICE software and more than most routers. In many scenarios, it would be possible to do no configuration at all and still obtain a secure connection to the Internet.
Because there's a Web-based interface, port 80 (HTTP) can be opened to allow administration from a remote site although the XRouter's port 80 is accessible only from the LAN interfaces by default. When a port scanner is aimed at the XRouter, the latest firmware doesn't even advertise the presence of the closed ports.
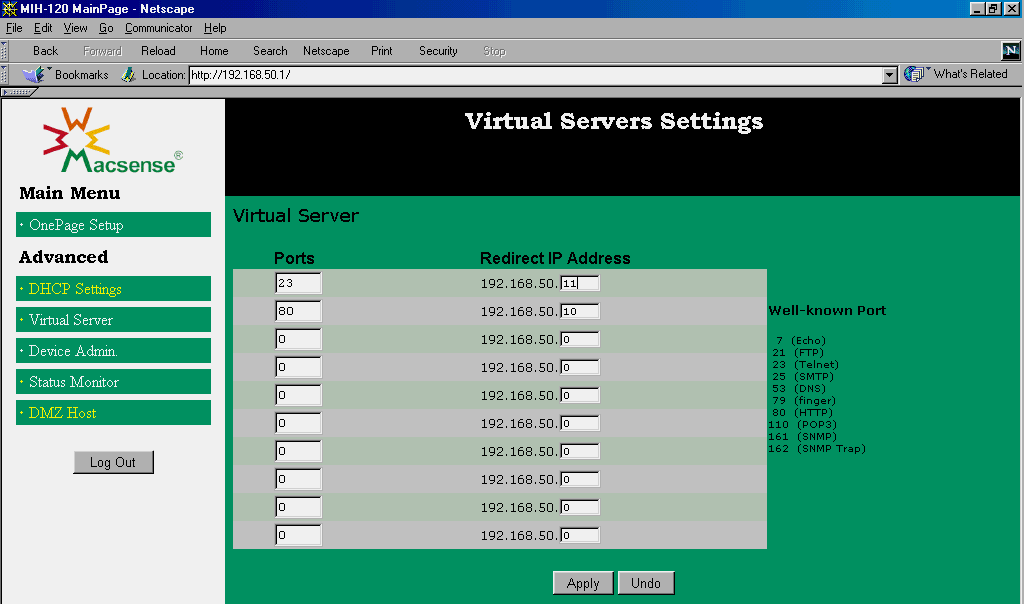
SCREEN 6. The XRouter Virtual Server Settings page allows configuring external access to internal servers.
|
The XRouter interface has six different pages relevant to cable modem configuration and only two relate to the firewall aspects of the device. The Virtual Servers Settings page (Screen 6) allows you to open ports in the firewall for specific protocols and to direct all incoming traffic that utilizes those ports to the appropriate server on the LAN. In the example in Screen 6, I was running Web server software on a computer with the private internal address of 192.168.50.10 and a Telnet server on the system with the address 192.168.50.11; it is my responsibility to lock down those services at those servers but this is a good security step because it prevents incoming traffic from going to the wrong server (as long as the addresses are configured correctly). Anyone attempting to Telnet to my public IP address would be routed to my Telnet server and anyone pointing their browser to my public IP address would be routed to my Web server.
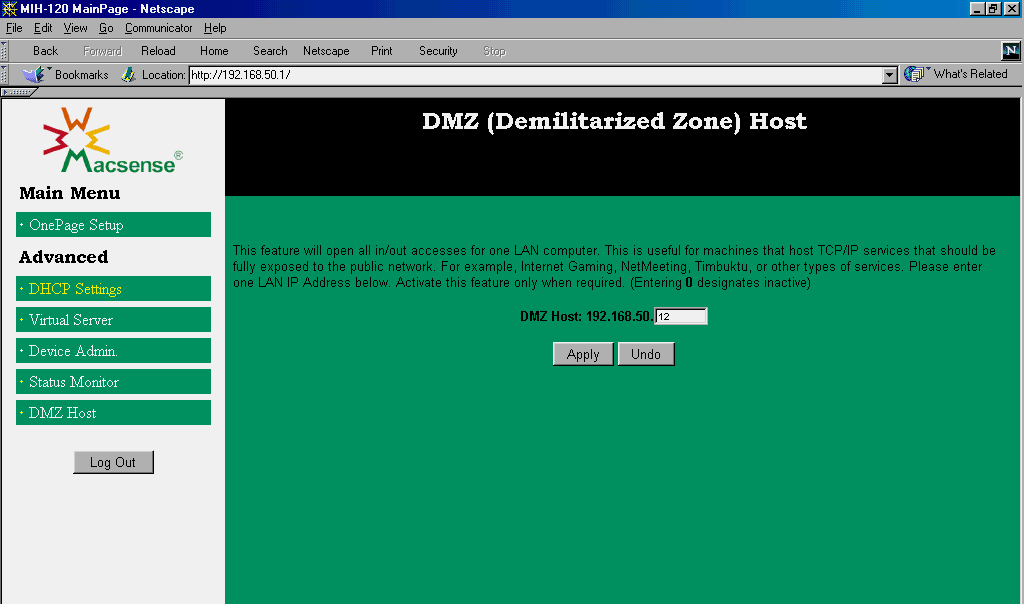
SCREEN 7. The XRouter DMZ Host page allows opening one system up to all protocols.
|
The DMZ Host page (Screen 7) provides for the definition of a single system that is the designated "DMZ host." This is another good security feature. If you have a system on your LAN that is providing only one or two services, the Virtual Server page makes the job of opening up the individual ports easy. But some useful services, such as NetMeeting, jump all over the map in terms of the ports that they use. Specifying a system as the DMZ host will allow complete protocol access to that host; again, it is the administrator's responsibility to provide adequate protection at that system. The management of the XRouter is simple enough that you can just open the DMZ host when you know its needed (e.g., when you know to accept an incoming NetMeeting connection) and then lock it up again once you're done with it.
The XRouter does a great job as a mini-router/hub/firewall but one thing that I thought was missing was the ability to log traffic. In addition, it has no intrusion detection nor notification capability. For a suitably small office, this is probably adequate; the XRouter will certainly keep pedestrian hackers out and will protect your network resources. But if you think that your site is a potential target for bad guys, it will not be able to let you know that you're under attack.
SUMMARY
Full-time, dedicated access to the Internet from small and home offices is on the rise. And the systems that are connected need as much protection as their counterparts on the corporate LAN, although the SOHO user probably doesn't have the time, expertise, or budget to provide the same level of protection.
Cable modem access has been (rightly) criticized as being potentially too open. The industry has responded with security protocols for the cable modem boxes; be sure that you get one that complies with these standards.
For the premises equipment, the SOHO security market provides two main avenues of protection — software firewalls for individual systems and low-cost firewall appliances. But why would you use one or the other?
My experience suggests that the software firewall is great as long as you are connecting one or two systems to the Internet. If you are connecting many computers to the network, I suggest the hardware approach because it is much easier to manage and administer; I think that attempting to load software consistently across multiple machines and platforms takes exponentially more time as you add systems!! Furthermore, firewall software for Windows systems (tested here) won't work on a Unix system or a Mac. If you do have a mixed operating system environment, the firewall hardware is great because you protect the network with a single device and don't have to touch any of the hosts.
If you have a small LAN and just want protection, go with the hardware solution; if you have one system and want to track people snooping, go with the software. Personally, I take a middle ground: the XRouter protects my network but I sometimes leave one system running BlackICE "open" at the router so that I can look at what's going on around me. It reminds me that there are no secure sites on the Internet, only vigilant ones!
One final observation. These are SOHO tools, in my opinion, not enterprise tools. BlackICE Defender is part of the ICEcap software suite from Network ICE that includes a more extensive reporting capability and network monitoring. I didn't get an opportunity to test the entire suite and if it is anything like BlackICE, the quality will be excellent. Nevertheless, I would not advise employing personal firewall software installed on every networked computer in lieu of a stand-alone firewall in an enterprise environment. And although the XRouter can logically handle 252 hosts on the network, I wouldn't recommend it as the firewall for the enterprise where configuration flexibility might be necessary.
But that's all fine as far as I am concerned because these products are targeted at the SOHO and I think that they hit that mark right on. Too many networks go unprotected ostensibly because of the cost. These two products together cost about $200 and demonstrate that there is no excuse to let your SOHO LAN go unprotected.
SIDEBAR:
Main items to address in your SOHO using cable modem access:
- Ensure that the cable modem complies with the DOCSIS BPI specification.
- Unbind file and print sharing from TCP/IP at all hosts unless it is required.
- Use additional precautions: firewall software and/or an external firewall appliance.
- Use NAT if possible. (Since most cable modem services only assign a single public IP address, this will be necessary if you have a LAN.)
About the Author: Gary C. Kessler is a network security analyst and educator living in Colchester, Vermont (http://www.garykessler.net). His e-mail addresses is kumquat@sover.net.







